Teksys is here to secure you Video Network from Cyber Attacks
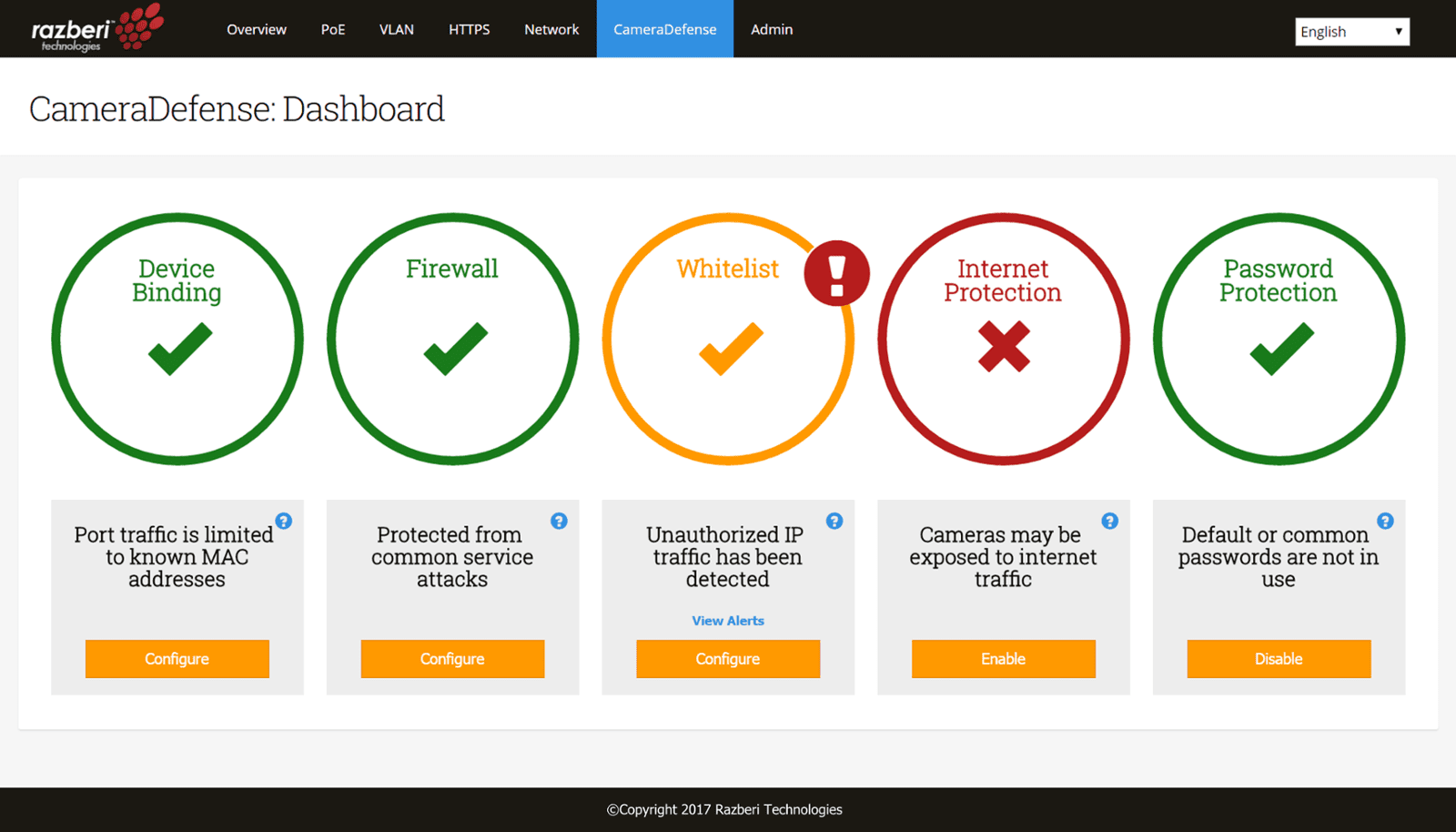
Thinking about cybersecurity in three key pillars, you are already ahead of the game. CameraDefense™
automates and scales your efforts. First, you’ll harden cameras automatically so they don’t become a liability. Next, you'll
use the unique capabilities of ServerSwitchIQ™ to isolate cameras in a distributed appliance architecture and set
up a VLAN. Then, you’ll take advantage of ongoing health monitoring for proactive alerts to act before it is too late.
Teksys & Razberi provides encryption-ready hardware and uses artificial intelligence by embedding CylancePROTECT® to protect
against antivirus and malware threats. Teksys makes it easy for you, hard for the hackers.
The Security of the Security
Hackers are relentless. They never stop looking for the next entry point into a network. Ironically, the surveillance cameras installed to protect and lower risk provide yet another window of opportunity. It’s keeping security leaders awake at night - but it doesn’t have to. With the right technology partner, you can be on the offense and defense to protect the surveillance system and to stop infiltration into the IP network and critical data.
What’s at stake is the organization’s brand reputation, millions of dollars and personally identifiable information.
It’s time to make sure that the camera is not a launch pad for attack with the right tools, automation and architecture.

